Published by: Zaya
Published date: 22 Jun 2021
An operating system might have many structures. According to the structure of the operating system; operating systems can be classified into many categories.
Some of the main structures used in operating systems are:
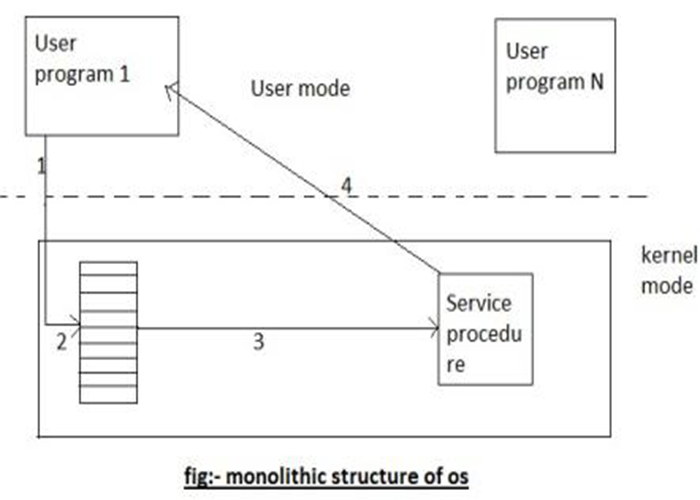
It is the oldest architecture used for developing operating systems. The operating system resides on the kernel for anyone to execute. A system call is involved i.e. Switching from user mode to kernel mode and transfer control to the operating system shown as event 1. Many CPU has two modes, kernel mode, for the operating system in which all instruction is allowed and user mode for user program in which I/O devices and certain other instruction are not allowed. Two operating systems then examine the parameter of the call to determine which system call is to be carried out shown in event 2. Next, the operating system indexes into a table that contains a procedure that carries out a system call. This operation is shown in events. Finally, it is called when the work has been completed and the system call is finished, control is given back to the user-mode as shown in event 4.
The layered architecture of the operating system was developed in the ’60s in this approach; the operating system is broken up into a number of layers. The bottom layer (layer 0) is the hardware layer and the highest layer (layer n) is the user interface layer as shown in the figure.
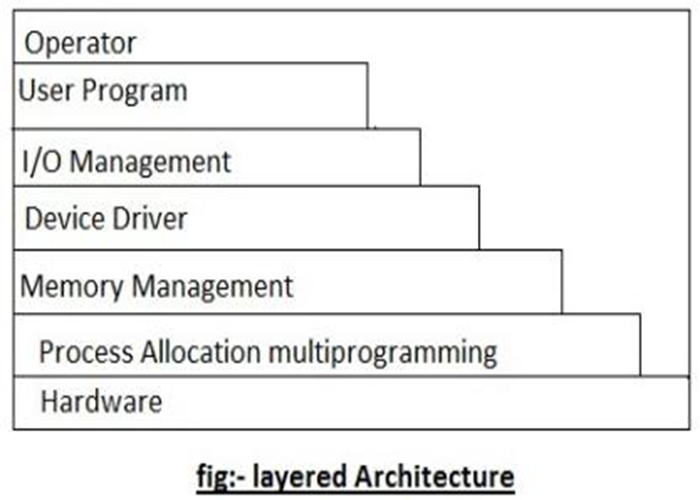
The layered are selected such that each user functions and services of only a lower-level layer. The first layer can be debugged without any concern for the rest of the system. It user basic hardware to implement this function once the first layer is debugged., its correct functioning can be assumed while the second layer is debugged & soon. If an error is found during the debugged of a particular layer, the layer must be on that layer, because the layer below it already debugged. Because of this design of the system is simplified when the Operating system is broken up into layers.
Os/2 operating system is an example of the layered architecture of operating system another example is an earlier version of Windows NT.
The main disadvantage of this architecture is that it requires an appropriate definition of the various layers & careful planning of the proper placement of the layer.
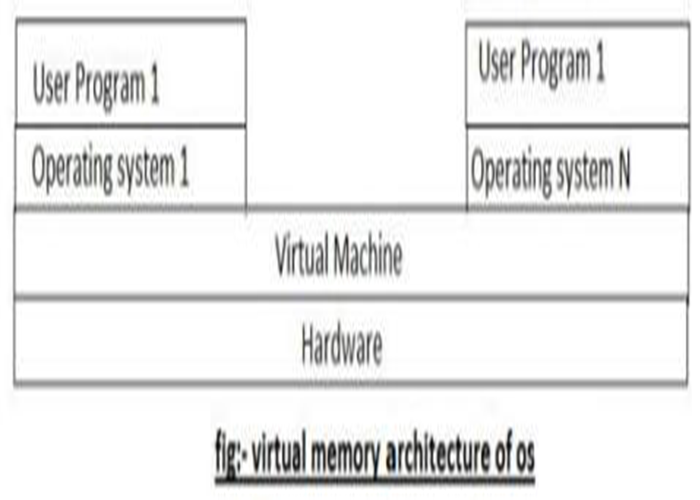
The virtual machine is an illusion of a real machine. It is created by a real machine operating system, which makes a single real machine appears to be several real machines. The architecture of the virtual machine is shown above.
The best example of virtual machine architecture is IBM 370 computer. In this system, each user can choose a different operating system. Actually, the virtual machine can run several operating systems at once, each of them on its virtual machine. Its multiprogramming shares the resource of a single machine in a different manner.
The concepts of the virtual machine are: -
a. Control program (cp): cp creates the environment in which virtual machines can execute. It gives to each user facilities of real machines such as processors, storage I/0 devices.
b. conversation monitor system (cons): -cons is a system application having features of developing the program. It contains editor, language translator, and various application packages.
c. Remote spooling communication system (RSCS): provide virtual machine with the ability to transmit and receive the file in a distributed system.
d. IPCS (interactive problem control system): it is used to fix virtual machine software problems.
A trend in the modern operating systems is to move maximum code to the higher level and remove as much as possible from the operating system, minimizing the work of the kernel. The basic approach is to implement most of the operating system functions in user processes to request a service, such as a request to read a particular file, the user sends a request to the server process, the server checks the parameter and finds whether it is valid or not after that server does the work and send back the answer to client-server model works on request-response technique i.e. Client always send a request to the side in order to perform the task, and on the other side, server gates complementing that request sends back response. The figure below shows the client-server architecture.
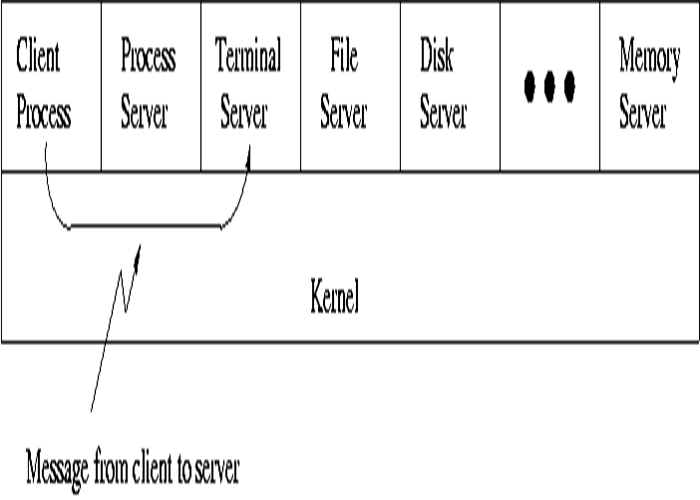
In this model, the main task of the kernel is to handle all the communication between the client and the server by splitting the operating system into a number of ports, each of which only handles some specific task i.e. file server, process server, terminal server, and memory service.
Another advantage of the client-server model is its adaptability to users in a distributed system. If the client communicates with the server by sending it the message, the client need not know whether it was sending a ……. Is the network to a server on a remote machine? As in the case of a client, the same thing happens and occurs in client-side that is a request was send and a reply come back.
Kernel mode and User mode
In any modern operating system, the CPU is actually spending time in two very distinct modes to make sure it works correctly:
Kernel Mode
In Kernel mode, the executing code has complete and unrestricted access to the underlying hardware. It can execute any CPU instruction and reference any memory address. Kernel mode is generally reserved for the lowest-level, most trusted functions of the operating system. Crashes in kernel mode are catastrophic; they will halt the entire PC.
User Mode
In User Mode, the executing code has no ability to directly access hardware or reference memory. Code running in user mode must delegate to system APIs to access hardware or memory. Due to the protection afforded by this sort of isolation, crashes in user mode are always recoverable. Most of the code running on your computer will execute in user mode.
The necessity of Dual Mode (User Mode and Kernel Mode) in Operating System
The lack of a dual-mode i.e. user mode and kernel mode in an operating system can cause serious
problems. Some of these are: